Bypassing the Login Screen: A Comprehensive Guide to Automating Windows 11 Startup
Related Articles: Bypassing the Login Screen: A Comprehensive Guide to Automating Windows 11 Startup
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Bypassing the Login Screen: A Comprehensive Guide to Automating Windows 11 Startup. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Bypassing the Login Screen: A Comprehensive Guide to Automating Windows 11 Startup

The convenience of a password-free Windows 11 startup is undeniable. It eliminates the need for repeated typing, streamlines the user experience, and can be particularly beneficial in shared environments or for users who find the login process cumbersome. However, it is crucial to understand the security implications and best practices associated with this approach before implementing it. This article provides a detailed explanation of the methods available for bypassing the login screen, their respective benefits and risks, and essential considerations for a secure and efficient user experience.
Understanding the Login Screen and its Purpose
The login screen acts as the first line of defense for your Windows 11 system. It ensures that only authorized users can access your data and applications. The password requirement serves as a barrier against unauthorized access, protecting your sensitive information from prying eyes.
Methods for Bypassing the Login Screen
There are several methods to bypass the login screen in Windows 11, each with its own advantages and disadvantages:
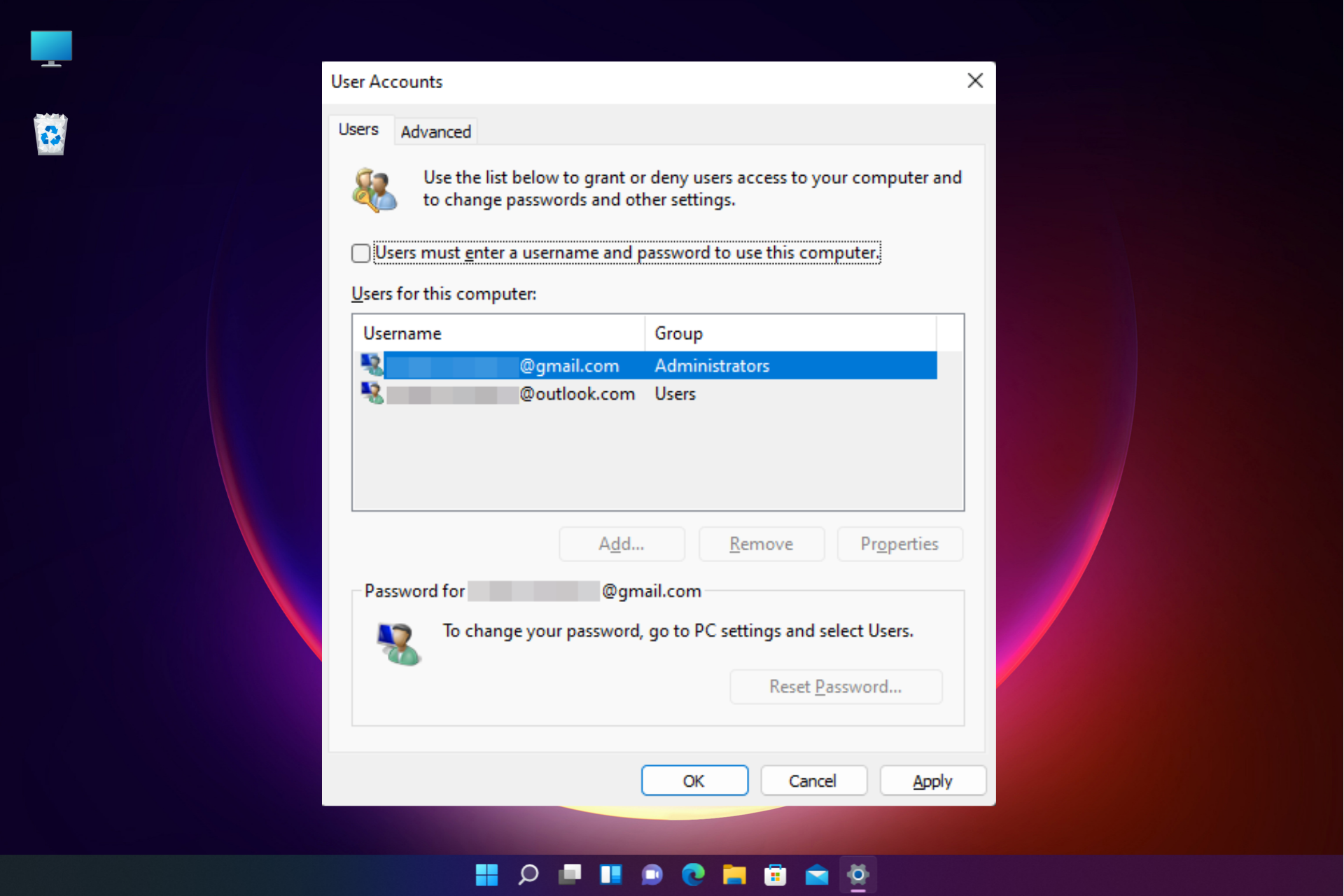
1. Using a Local Account without a Password:
This method involves creating a local user account without setting a password. This allows you to log in directly without entering any credentials.
Advantages:
- Simplicity: This is the easiest and most straightforward method for bypassing the login screen.
- Immediate Access: You can access your system without any delays.
Disadvantages:
- Security Risks: This method significantly compromises your system’s security, as anyone with physical access to your computer can log in without needing a password.
- Limited Functionality: You may not have access to certain features or settings that require administrator privileges.
2. Using a Microsoft Account without a Password:
Similar to the local account method, you can create a Microsoft account without a password. This allows you to log in using your email address and a verification code.
Advantages:
- Cloud Integration: Your account data is synced with your Microsoft account, providing access to your files and settings across multiple devices.
- Two-Factor Authentication: You can enhance security by enabling two-factor authentication, requiring a code from your mobile device for login.
Disadvantages:
- Security Concerns: Although two-factor authentication provides an additional layer of security, it is still vulnerable to phishing attacks and social engineering.
- Limited Control: You might not have full control over your system’s settings and configurations.
3. Using a Password Manager:
Password managers can store your passwords securely and automatically enter them during login.
Advantages:
- Convenience: You only need to remember a single master password for the password manager.
- Stronger Security: Password managers often generate and store complex passwords, enhancing your overall security.
Disadvantages:
- Potential Security Risks: If your master password is compromised, all your stored passwords are at risk.
- Dependency: You need to have the password manager installed and configured on your system.
4. Using the "net user" Command:
This method involves using the command prompt to disable the password requirement for a specific user account.
Advantages:
- Flexibility: You can choose to disable the password requirement for specific user accounts, allowing for granular control over access.
- Advanced Users: This method is ideal for users familiar with command-line interfaces.
Disadvantages:
- Security Risks: This method is highly insecure and exposes your system to unauthorized access.
- Technical Knowledge Required: This method requires a basic understanding of command-line commands.
5. Using the "Local Security Policy" Editor:
This method allows you to modify the system’s security settings, including the requirement for a password during login.
Advantages:
- System-Wide Control: You can manage the password requirement for all user accounts from a central location.
- Advanced Settings: The Local Security Policy editor offers a wide range of security settings that can be customized.
Disadvantages:
- Complex Settings: The Local Security Policy editor is complex and requires a thorough understanding of security settings.
- Security Risks: Improper configuration can compromise your system’s security.
6. Using the "Automatic Login" Feature:
This feature allows you to automatically log in to your account without requiring a password.
Advantages:
- Convenience: You can access your system immediately without any user interaction.
- Shared Environments: This is particularly useful in shared environments, such as public computers or kiosks.
Disadvantages:
- Security Risks: This method significantly compromises your system’s security, as anyone with physical access to your computer can log in without a password.
- Limited Control: You cannot prevent unauthorized access while the computer is unattended.
7. Using Third-Party Software:
There are various third-party software solutions available that can bypass the login screen, offering additional features and customization options.
Advantages:
- Customization: Some software offers advanced features like delayed login, automatic shutdown, or specific account restrictions.
- User-Friendly Interface: Many third-party tools offer intuitive interfaces for managing login settings.
Disadvantages:
- Security Risks: Using third-party software can introduce security vulnerabilities if not sourced from reputable developers.
- Compatibility Issues: Some software might not be compatible with all versions of Windows 11.
Important Considerations Before Bypassing the Login Screen
Before implementing any of the above methods, carefully consider the following:
- Security: Always prioritize security over convenience. Avoid methods that compromise your system’s security.
- Account Type: Understand the differences between local and Microsoft accounts and their respective security implications.
- Shared Environments: If you are using a shared computer, avoid disabling the password requirement.
- Alternative Solutions: Explore other solutions, such as a biometric login system or a password manager, that balance security and convenience.
FAQs
Q: Is it safe to bypass the login screen in Windows 11?
A: Bypassing the login screen can significantly compromise your system’s security. It is generally not recommended unless you have a specific need and understand the associated risks.
Q: Can I bypass the login screen using a USB drive?
A: Yes, there are methods that involve using a USB drive to bypass the login screen. However, these methods are often complex and require advanced technical knowledge.
Q: What are the best practices for securing my system after bypassing the login screen?
A: If you choose to bypass the login screen, consider implementing additional security measures, such as:
- Strong Passwords: Use strong passwords for your accounts and change them regularly.
- Two-Factor Authentication: Enable two-factor authentication for your accounts to enhance security.
- Antivirus Software: Install and maintain a reliable antivirus software to protect your system from malware.
- Firewall: Enable your system’s firewall to block unauthorized access.
- Regular Updates: Keep your system and software up to date with the latest security patches.
Tips
- Use a Local Account with a Strong Password: If you need to bypass the login screen for convenience, create a local account with a strong password.
- Enable Two-Factor Authentication: If you are using a Microsoft account, enable two-factor authentication for enhanced security.
- Use a Password Manager: Consider using a password manager to store and manage your passwords securely.
- Monitor System Activity: Regularly monitor your system for any unusual activity or suspicious software.
Conclusion
Bypassing the login screen in Windows 11 can offer convenience, but it comes with significant security risks. It is essential to weigh the benefits against the potential drawbacks before implementing any method. If you choose to bypass the login screen, prioritize security measures and take steps to minimize the risks associated with this approach. Remember, a secure system is a fundamental requirement for protecting your data and privacy.






Closure
Thus, we hope this article has provided valuable insights into Bypassing the Login Screen: A Comprehensive Guide to Automating Windows 11 Startup. We hope you find this article informative and beneficial. See you in our next article!
