Securing Your Digital Fortress: A Comprehensive Guide to Windows Full Disk Encryption
Related Articles: Securing Your Digital Fortress: A Comprehensive Guide to Windows Full Disk Encryption
Introduction
With great pleasure, we will explore the intriguing topic related to Securing Your Digital Fortress: A Comprehensive Guide to Windows Full Disk Encryption. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Securing Your Digital Fortress: A Comprehensive Guide to Windows Full Disk Encryption

In the digital age, where data is the lifeblood of individuals and organizations alike, safeguarding sensitive information has become paramount. Data breaches and cyberattacks are increasingly common, posing a significant threat to privacy, security, and financial stability. Windows full disk encryption emerges as a powerful defense mechanism, providing an impenetrable shield for the data residing on your computer. This comprehensive guide delves into the intricacies of full disk encryption, exploring its functionalities, benefits, and implications in detail.
Understanding the Fundamentals of Full Disk Encryption
Full disk encryption, as the name suggests, encrypts the entire contents of a hard drive, including the operating system, applications, and user files. This encryption process transforms data into an unreadable format, rendering it inaccessible to unauthorized individuals. The decryption key, which is essential for accessing the encrypted data, is typically stored securely within the computer’s hardware or in a separate location.
The Encryption Process: A Step-by-Step Overview
The encryption process involves the following steps:
-
Key Generation: A unique encryption key is generated, serving as the password for unlocking the encrypted data.
-
Data Transformation: The encryption algorithm, such as Advanced Encryption Standard (AES), scrambles the data on the hard drive, converting it into an indecipherable format.
-
Key Storage: The encryption key is stored securely, either within the computer’s Trusted Platform Module (TPM) or in a separate location like a password manager.
-
Decryption: Upon system boot, the decryption key is retrieved and used to decrypt the data, allowing the operating system and applications to access the data.
The Benefits of Windows Full Disk Encryption
Implementing full disk encryption on a Windows computer offers a multitude of advantages:
-
Data Protection: Full disk encryption acts as a robust shield against unauthorized access, preventing data theft or manipulation even if the physical device falls into the wrong hands.
-
Compliance with Regulations: Many industries and organizations are subject to stringent data protection regulations, such as HIPAA for healthcare and PCI DSS for payment card processing. Full disk encryption ensures compliance with these regulations, minimizing legal and financial risks.
-
Increased Security: By encrypting the entire hard drive, full disk encryption significantly enhances the security posture of a computer, making it more resistant to malware, ransomware, and other cyber threats.
-
Peace of Mind: Knowing that sensitive data is protected by strong encryption provides peace of mind, allowing individuals and organizations to focus on their core activities without worrying about data breaches.
Types of Windows Full Disk Encryption
Windows offers several options for implementing full disk encryption:
-
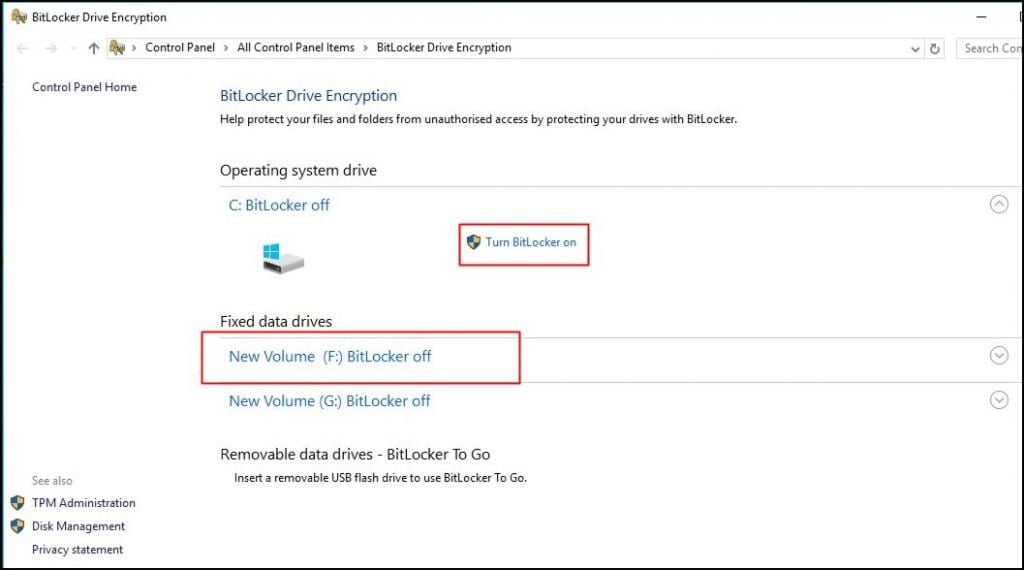
BitLocker: A built-in encryption feature available in Windows 10 and Windows 11, BitLocker provides robust encryption for both internal and external drives.
-
Microsoft Azure Disk Encryption: A cloud-based encryption service offered by Microsoft, Azure Disk Encryption enables the encryption of virtual disks in Azure environments.
-
Third-Party Solutions: Several third-party software vendors offer full disk encryption solutions, providing additional features and customization options.
Factors to Consider When Choosing a Full Disk Encryption Solution
When selecting a full disk encryption solution, several factors should be taken into account:
-
Compatibility: Ensure the chosen solution is compatible with your operating system and hardware.
-
Performance: Encryption can impact system performance, especially on older hardware. Consider the performance implications of the chosen solution.
-
Features: Evaluate the features offered by different solutions, such as encryption strength, key management options, and support for multiple drives.
-
Ease of Use: Choose a solution that is user-friendly and easy to manage.
-
Cost: Consider the cost of the solution, including licensing fees and support costs.
FAQs About Windows Full Disk Encryption
1. Is full disk encryption necessary for all users?
While full disk encryption offers significant benefits, it may not be necessary for all users. If your data is not sensitive or you are not concerned about data breaches, full disk encryption may not be a priority. However, for individuals and organizations handling sensitive information, it is highly recommended.
2. Can I use full disk encryption on external drives?
Yes, full disk encryption can be applied to external drives. BitLocker, for example, supports encryption for both internal and external drives.
3. How secure is full disk encryption?
Full disk encryption, when properly implemented, provides a high level of security. However, the effectiveness of encryption depends on the strength of the encryption algorithm and the security of the encryption key.
4. What happens if I forget my encryption password?
If you forget your encryption password, you may lose access to your data. It is crucial to store your password securely and to have a backup plan in case you forget it.
5. Can I encrypt only specific files or folders?
While full disk encryption encrypts the entire drive, you can use file and folder encryption tools to encrypt specific data. However, this approach may not provide the same level of protection as full disk encryption.
Tips for Implementing and Managing Full Disk Encryption
-
Choose a strong password: When setting up full disk encryption, use a strong password that is at least 12 characters long and includes a combination of uppercase and lowercase letters, numbers, and symbols.
-
Enable automatic encryption: Configure your encryption solution to automatically encrypt data when the computer is idle or in sleep mode.
-
Back up your data: Regularly back up your data to an external drive or cloud storage service. This ensures that you can recover your data in case of a data loss event.
-
Keep your encryption software updated: Regularly update your encryption software to ensure that it is protected against the latest security threats.
-
Monitor encryption status: Regularly check the encryption status of your drives to ensure that they are properly protected.
Conclusion
Full disk encryption is an essential security measure for safeguarding sensitive data on Windows computers. It provides a powerful defense against unauthorized access, data breaches, and cyber threats. By implementing full disk encryption and following best practices, individuals and organizations can significantly enhance their data security posture and protect their valuable assets.





Closure
Thus, we hope this article has provided valuable insights into Securing Your Digital Fortress: A Comprehensive Guide to Windows Full Disk Encryption. We thank you for taking the time to read this article. See you in our next article!
