The Unseen Threat: Exploring the Consequences of Missing Security Measures in Modern Devices
Related Articles: The Unseen Threat: Exploring the Consequences of Missing Security Measures in Modern Devices
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Unseen Threat: Exploring the Consequences of Missing Security Measures in Modern Devices. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Unseen Threat: Exploring the Consequences of Missing Security Measures in Modern Devices

In the digital age, devices have become ubiquitous, seamlessly woven into the fabric of our lives. From smartphones and laptops to smart home appliances and even cars, technology empowers us, connects us, and simplifies our daily routines. However, this digital interconnectedness comes with a hidden cost: vulnerability. The absence of robust security measures in these devices creates a landscape ripe for exploitation, leaving users susceptible to a range of threats, from data breaches and financial losses to identity theft and even physical harm.
This article delves into the critical importance of security in modern devices, exploring the consequences of neglecting essential safeguards. It examines the various vulnerabilities that arise from missing security measures, highlighting the potential risks and providing actionable insights for mitigating these threats.
The Landscape of Digital Vulnerability
The modern device landscape is characterized by a complex interplay of hardware, software, and network connectivity. This intricate ecosystem presents numerous points of entry for malicious actors, making security a paramount concern.
1. Software Vulnerabilities:
Software, the lifeblood of any device, is often riddled with vulnerabilities. These flaws, often overlooked during development or introduced through subsequent updates, can be exploited by attackers to gain unauthorized access, steal data, or even take complete control of the device.
- Unpatched Software: Many devices operate on outdated software versions that lack the latest security patches. These patches address known vulnerabilities, but neglecting updates leaves devices exposed to exploitation.
- Weak Encryption: Inadequate encryption algorithms or improper implementation can expose sensitive data, such as passwords, financial information, and personal communications, to unauthorized access.
- Unsecured Communication Channels: Communication between devices, especially over public networks, should be encrypted to prevent eavesdropping and data interception. Failure to implement secure protocols leaves communication vulnerable to malicious actors.
2. Hardware Vulnerabilities:
Hardware components, while seemingly robust, can also harbor vulnerabilities. These vulnerabilities can be exploited to bypass security measures, tamper with device functionality, or even extract sensitive data.
- Hardware Trojans: Malicious hardware components, intentionally introduced during manufacturing or supply chain compromises, can provide attackers with backdoor access to devices.
- Side-Channel Attacks: These attacks exploit physical characteristics of devices, such as power consumption or electromagnetic emissions, to extract sensitive information or bypass security mechanisms.
3. Network Vulnerabilities:
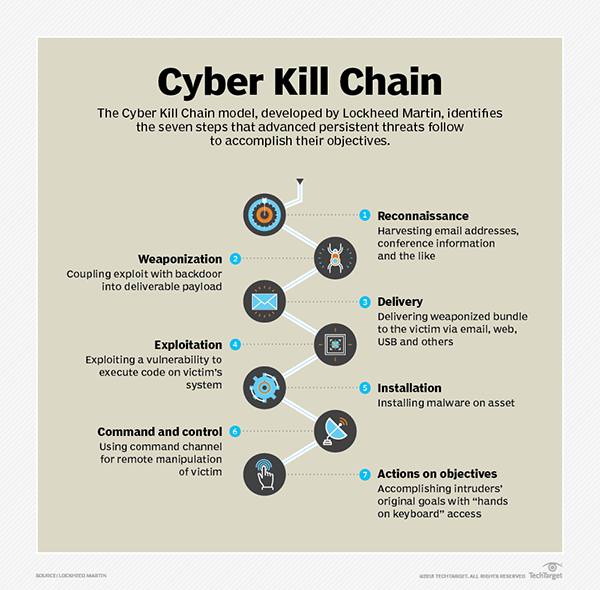
The interconnected nature of modern devices exposes them to network vulnerabilities. These vulnerabilities can be exploited to gain access to devices, intercept communications, or even launch attacks against other devices on the network.
- Unsecured Wi-Fi Networks: Public Wi-Fi networks are often poorly secured, making them easy targets for attackers to intercept data or inject malicious software.
- Man-in-the-Middle Attacks: These attacks intercept communication between devices, allowing attackers to eavesdrop on data or even manipulate communication to steal credentials or inject malicious code.
The Consequences of Missing Security Measures
The consequences of neglecting security in modern devices can be far-reaching and devastating, impacting individuals, businesses, and even national security.
1. Data Breaches and Financial Loss:
Data breaches are a common occurrence in the digital age, with attackers targeting sensitive information such as financial data, personal details, and intellectual property. The consequences of such breaches can be severe, leading to financial loss, identity theft, and reputational damage.
2. Identity Theft and Fraud:
Missing security measures can expose personal information, making individuals vulnerable to identity theft and fraud. Attackers can use stolen data to open credit cards, take out loans, or even commit crimes in the victim’s name.
3. Denial of Service and System Disruption:
Attackers can exploit vulnerabilities to launch denial-of-service attacks, overwhelming devices or networks with traffic, rendering them unusable. This can disrupt critical services, causing financial losses and affecting productivity.
4. Espionage and National Security Threats:
In the realm of national security, compromised devices can be used to gather intelligence, conduct espionage, or even disrupt critical infrastructure. The consequences of such attacks can be devastating, impacting national security and economic stability.
5. Physical Harm and Safety Risks:
In an increasingly connected world, vulnerabilities in devices can pose physical harm and safety risks. For example, compromised medical devices could malfunction, endangering patients, while compromised vehicles could be remotely controlled, leading to accidents.
Mitigating the Risks: A Multifaceted Approach
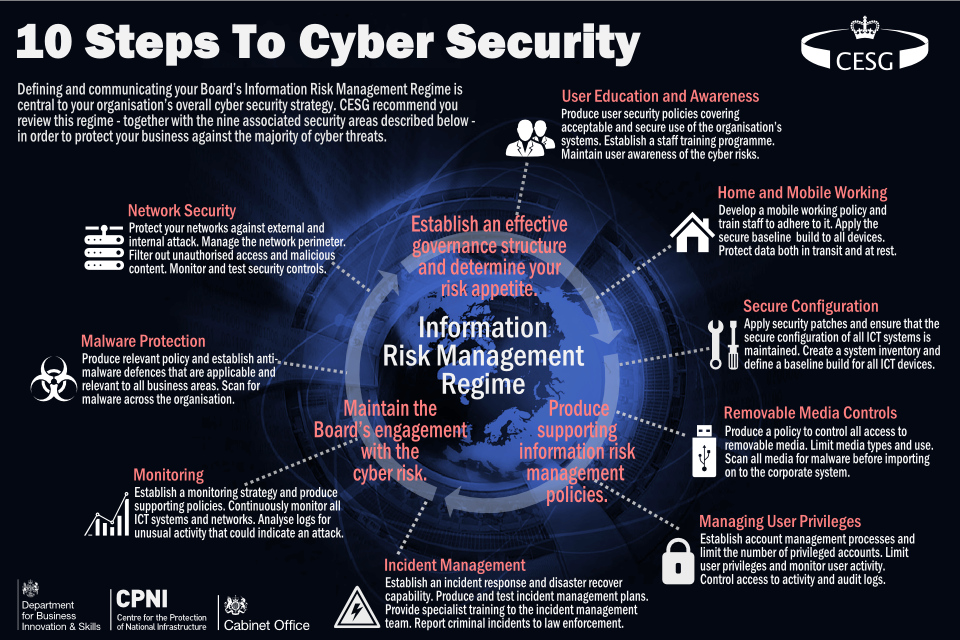
Addressing the security challenges posed by modern devices requires a multifaceted approach that encompasses individual user responsibility, robust security practices by device manufacturers, and proactive measures by governments and regulatory bodies.
1. User Responsibility:
- Software Updates: Regularly update software on all devices to patch vulnerabilities and improve security.
- Strong Passwords: Use strong, unique passwords for all accounts and avoid reusing passwords across multiple platforms.
- Multi-factor Authentication: Enable multi-factor authentication whenever possible to add an extra layer of security.
- Secure Wi-Fi Networks: Use strong passwords for home Wi-Fi networks and avoid connecting to public Wi-Fi networks without using a VPN.
- Be Cautious of Phishing Attempts: Be wary of suspicious emails, messages, or websites that request personal information.
- Use Anti-Virus Software: Install and regularly update anti-virus software to detect and remove malware.
2. Device Manufacturer Responsibility:
- Secure Development Practices: Implement robust security practices during the development lifecycle to minimize vulnerabilities.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Transparency and Disclosure: Be transparent about vulnerabilities and promptly disclose them to users and security researchers.
- Secure Updates: Release regular security updates to address vulnerabilities and enhance security.
3. Government and Regulatory Body Responsibility:
- Security Standards and Regulations: Establish clear security standards and regulations for device manufacturers and service providers.
- Cybersecurity Awareness Campaigns: Conduct public awareness campaigns to educate users about cybersecurity threats and best practices.
- Cybersecurity Research and Development: Invest in cybersecurity research and development to advance security technologies and address emerging threats.
FAQs
Q: What are the most common security vulnerabilities in modern devices?
A: Common vulnerabilities include unpatched software, weak encryption, unsecured communication channels, hardware Trojans, side-channel attacks, and insecure Wi-Fi networks.
Q: How can I protect myself from data breaches and identity theft?
A: Use strong passwords, enable multi-factor authentication, be cautious of phishing attempts, use anti-virus software, and keep software updated.
Q: What are the consequences of neglecting security in medical devices?
A: Compromised medical devices could malfunction, endangering patients.
Q: How can governments and regulatory bodies improve cybersecurity?
A: By establishing security standards and regulations, conducting cybersecurity awareness campaigns, and investing in cybersecurity research and development.
Tips
- Educate Yourself: Stay informed about cybersecurity threats and best practices.
- Be Proactive: Take steps to secure your devices and accounts.
- Be Vigilant: Be wary of suspicious activities and report any security incidents.
- Use Security Tools: Utilize anti-virus software, firewalls, and other security tools.
- Stay Updated: Regularly update software and firmware on your devices.
Conclusion
The absence of robust security measures in modern devices poses a significant threat to individuals, businesses, and national security. By understanding the vulnerabilities, consequences, and mitigation strategies, we can collectively work towards a more secure digital landscape. It is imperative that users, device manufacturers, governments, and regulatory bodies collaborate to address this pressing issue and ensure the safe and responsible use of technology. Only through a concerted effort can we protect ourselves from the unseen threats lurking in the digital realm.





Closure
Thus, we hope this article has provided valuable insights into The Unseen Threat: Exploring the Consequences of Missing Security Measures in Modern Devices. We thank you for taking the time to read this article. See you in our next article!
