The Windows Security Quarantine: A Safe Haven for Suspicious Files
Related Articles: The Windows Security Quarantine: A Safe Haven for Suspicious Files
Introduction
With great pleasure, we will explore the intriguing topic related to The Windows Security Quarantine: A Safe Haven for Suspicious Files. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Windows Security Quarantine: A Safe Haven for Suspicious Files

In the digital landscape, threats are ever-present. Malware, viruses, and other malicious software constantly seek to infiltrate systems, compromising data and disrupting operations. Windows, as a dominant operating system, has implemented robust security measures to combat these threats, and one such crucial component is the quarantine folder.
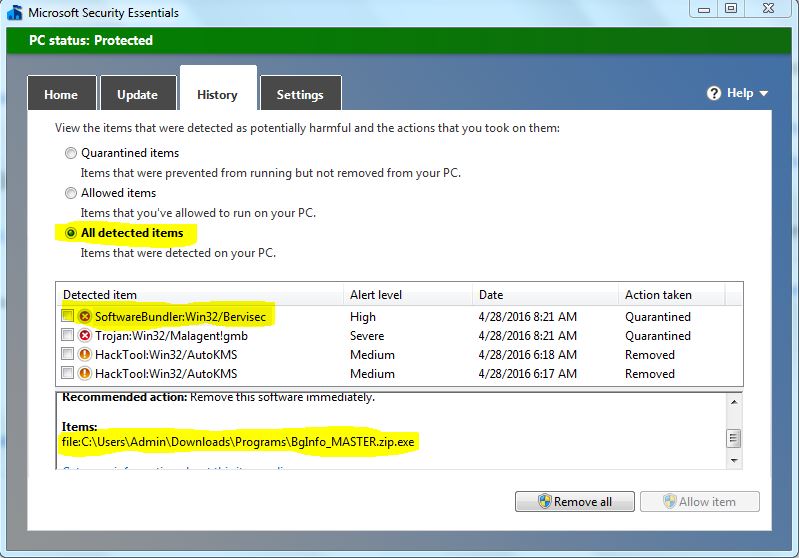
The quarantine folder acts as a secure holding area for files deemed potentially harmful by Windows security systems. These files are isolated from the rest of the system, preventing them from executing or causing damage. This isolation mechanism provides a critical layer of protection, allowing users to investigate the quarantined files and decide on appropriate action.
Understanding the Quarantine Process
When Windows detects a file that exhibits suspicious behavior or matches known malware signatures, it initiates the quarantine process. This process involves:
-
Detection: Windows security software, such as Windows Defender or third-party antivirus programs, actively scans the system for potential threats. This scanning can occur in real-time as files are accessed or downloaded, or through scheduled scans.
-
Isolation: If a file is flagged as suspicious, it is moved to the quarantine folder. This folder is typically located within the Windows directory, hidden from casual view.
-
Notification: Windows will usually notify the user about the quarantined file, providing information about the potential threat and the reason for isolation.
The Importance of the Quarantine Folder
The quarantine folder plays a vital role in safeguarding the user’s system and data. Its significance can be understood through these key benefits:
-
Preventing Malware Execution: By isolating suspicious files, the quarantine folder prevents them from executing and potentially causing damage to the system. This is crucial for preventing malware from spreading, corrupting data, or stealing sensitive information.
-
Allowing for Investigation: The quarantine folder provides a safe environment for users to investigate the quarantined files. Users can examine the file properties, scan it with alternative antivirus software, or seek information about the file online. This investigation helps determine if the file is truly malicious or a false positive.
-
Restoring Files: In some cases, quarantined files may be legitimate but mistakenly flagged as suspicious. The quarantine folder allows users to restore these files to their original locations, ensuring they are not unnecessarily blocked.
-
Maintaining System Integrity: By isolating potentially harmful files, the quarantine folder helps maintain the integrity of the system. It prevents malicious software from modifying system files, corrupting data, or interfering with system processes.
Navigating the Quarantine Folder
While the quarantine folder is typically hidden, users can access it through various means. Here are some common methods:
-
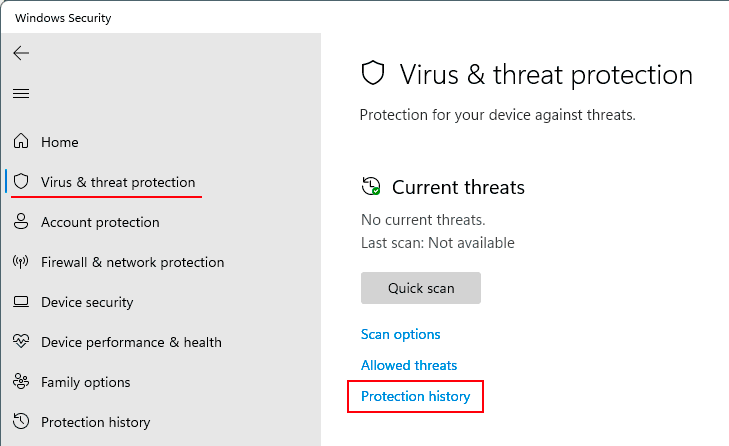
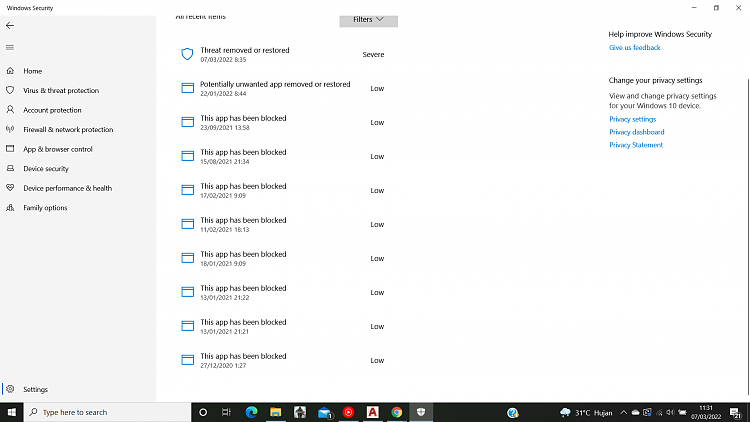
Windows Defender: Users can access the quarantine folder through the Windows Defender interface. This allows them to view quarantined files, restore them, or permanently delete them.
-
Third-Party Antivirus Software: Many third-party antivirus programs provide their own quarantine management tools, allowing users to interact with quarantined files directly.
-
File Explorer: Users can manually navigate to the quarantine folder by using File Explorer. However, this method requires knowing the exact location of the folder, which may vary depending on the security software used.
Frequently Asked Questions
Q: How do I know if a file is truly malicious?
A: While Windows security software provides a strong first line of defense, it’s essential to exercise caution. If a file is quarantined, it’s recommended to:
- Verify the file’s origin: Check if the file came from a trusted source, like a reputable website or a known application.
- Scan the file with multiple antivirus programs: Using different antivirus software can provide a more comprehensive analysis.
- Research the file online: Search for information about the file’s name or hash value to see if it has been identified as malicious.
Q: What should I do with quarantined files?
A: The appropriate action depends on the file’s nature and the user’s confidence in its legitimacy. Options include:
- Restore: If the file is considered safe, it can be restored to its original location.
- Delete: If the file is confirmed to be malicious, it should be permanently deleted from the quarantine folder.
- Report: If the user suspects the file might be a false positive, they can report it to the security software vendor or a reputable online security forum.
Q: Can I disable the quarantine feature?
A: While it’s technically possible to disable the quarantine feature, it is strongly discouraged. Disabling this critical security measure leaves the system vulnerable to malware attacks.
Tips for Effective Quarantine Management
- Regularly review the quarantine folder: Check the folder periodically to see if any new files have been quarantined. This allows for prompt action to remove malicious files or restore legitimate ones.
- Keep security software updated: Ensure that Windows Defender or any third-party antivirus software is updated regularly to receive the latest malware definitions.
- Be cautious about downloads: Only download files from trusted sources and be wary of suspicious emails or attachments.
- Use strong passwords: Protect your system from unauthorized access by using strong passwords and enabling two-factor authentication.
Conclusion
The Windows security quarantine folder is an essential component of a robust security system. It provides a safe haven for suspicious files, preventing them from executing and causing harm. By understanding the quarantine process, the importance of the folder, and the available management tools, users can effectively leverage this feature to enhance their system’s security and protect their valuable data.
While the quarantine folder offers a valuable line of defense, it’s important to remember that it is not a foolproof solution. Users should practice safe computing habits, keep their security software updated, and remain vigilant against potential threats. By combining these measures, users can significantly reduce the risk of malware infections and maintain a secure computing environment.


Closure
Thus, we hope this article has provided valuable insights into The Windows Security Quarantine: A Safe Haven for Suspicious Files. We hope you find this article informative and beneficial. See you in our next article!