Understanding User Activity on Windows: A Comprehensive Guide
Related Articles: Understanding User Activity on Windows: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Understanding User Activity on Windows: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding User Activity on Windows: A Comprehensive Guide
In the digital landscape, where data security and system integrity are paramount, understanding user activity on a Windows system is crucial. Knowing who is logged in, when, and from where provides valuable insights for administrators and users alike. This information empowers informed decision-making, enabling proactive security measures, troubleshooting issues, and ensuring efficient resource management.
Methods for Determining Logged-In Users
Windows offers several methods to determine who is currently logged in, each catering to different needs and levels of detail.
1. Task Manager:
The Task Manager, accessible through Ctrl+Shift+Esc or right-clicking the taskbar and selecting "Task Manager," provides a concise overview of running processes and active users. The "Users" tab within the Task Manager displays a list of currently logged-in users, including their username, session ID, and the time they logged in.
2. Command Prompt:
The command prompt, accessed by typing "cmd" in the search bar, offers command-line utilities for advanced system management. The command quser displays information about logged-in users, including their username, session ID, logon time, and the server they are connected to.
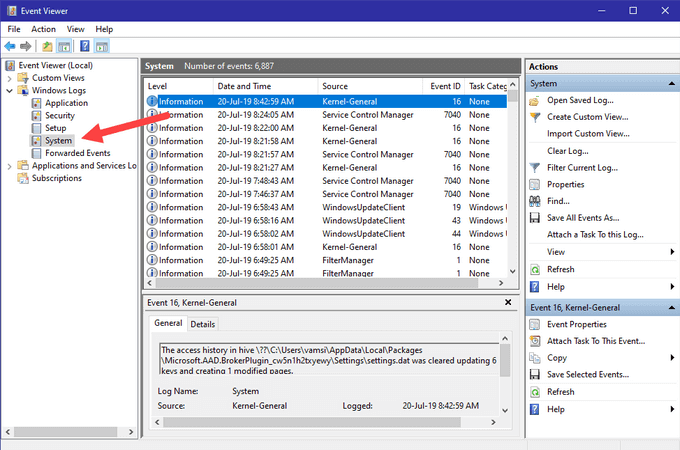
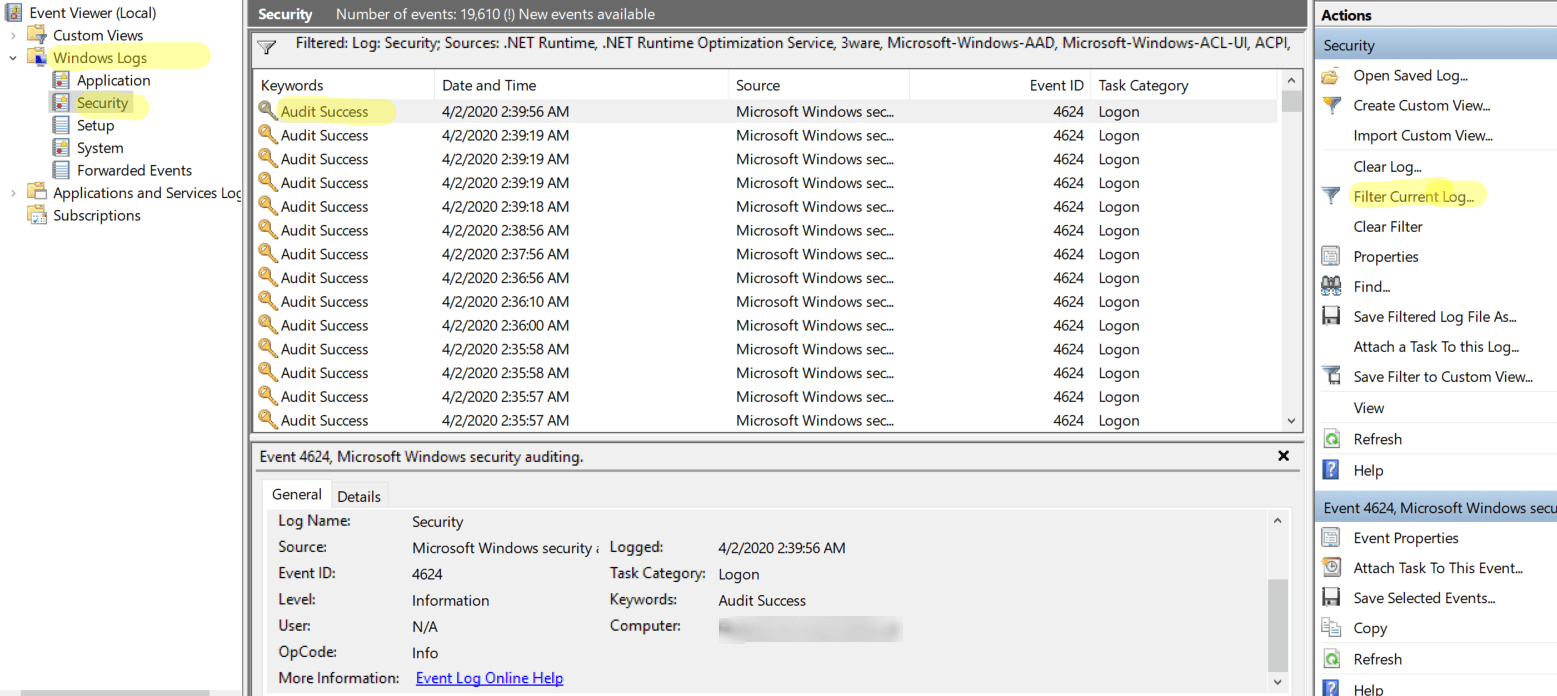
3. Event Viewer:
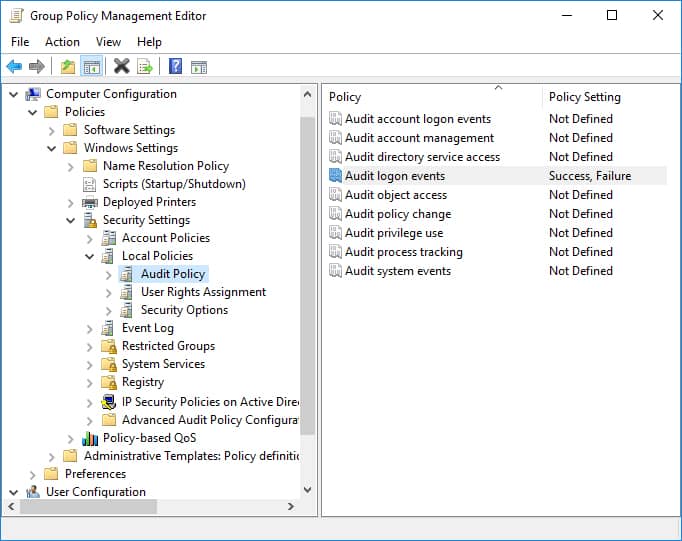
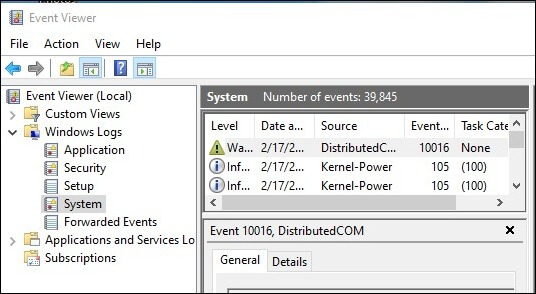
The Event Viewer, accessible by searching for "Event Viewer" in the search bar, provides a detailed log of system events, including user login and logout events. By navigating to "Windows Logs" > "Security," users can review event IDs 4624 (successful logon) and 4625 (failed logon) to track user activity.
4. System Information:
The System Information tool, accessible by searching for "System Information" in the search bar, provides a comprehensive overview of the system’s configuration and hardware. The "System Summary" section displays the current logged-in user.
5. Remote Desktop Connection:
When connecting to a remote computer via Remote Desktop Connection, the "Users" tab in the "Remote Desktop Connection" window displays the users currently logged in to the remote computer.
Benefits of Knowing Who is Logged In
Understanding user activity on a Windows system offers numerous benefits:
- Security Enhancement: Identifying unauthorized users or unusual login attempts enables timely security interventions, mitigating potential threats and data breaches.
- Resource Management: Monitoring user activity helps identify resource-intensive users and processes, facilitating efficient resource allocation and optimization.
- Troubleshooting: Tracking user logins assists in diagnosing system issues related to user profiles, permissions, or software conflicts.
- Accountability: Maintaining a record of user activity provides accountability for actions taken on the system, aiding in incident investigations and resolving disputes.
- Compliance: In regulated environments, tracking user activity is essential for compliance with industry standards and regulations regarding data security and user access.
FAQs
Q: How can I see the history of logged-in users?
A: While Windows doesn’t natively store a comprehensive history of logged-in users, utilizing the Event Viewer can provide insights into past login attempts. Analyzing event IDs 4624 and 4625 in the "Security" log can reveal successful and failed login attempts, offering a glimpse into user activity over time.
Q: How can I restrict user access to specific resources?
A: Windows offers robust user account management features. By creating user accounts with specific permissions, administrators can control access to files, folders, programs, and network resources. This ensures that only authorized users can access sensitive data and resources.
Q: What are the best practices for managing user accounts?
A: Implementing strong password policies, regularly reviewing user permissions, and enforcing multi-factor authentication are crucial for secure user account management. Regularly reviewing user activity and promptly disabling inactive accounts further enhances security.
Tips
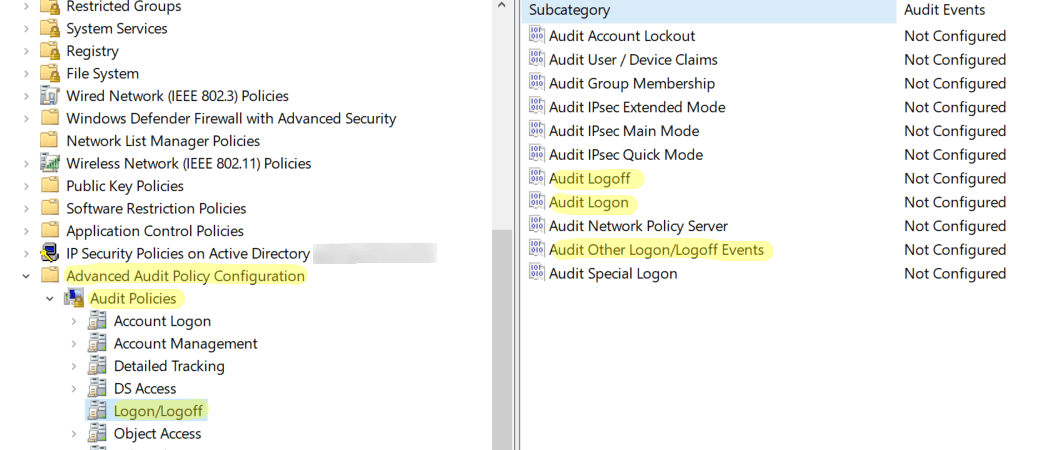
- Enable auditing: Configure Windows to audit user login events, capturing detailed information about successful and failed login attempts.
- Implement strong password policies: Enforce strong password requirements, including length, complexity, and regular password changes.
- Use multi-factor authentication: Require users to provide two or more forms of authentication, such as passwords and one-time codes, for enhanced security.
- Regularly review user permissions: Ensure that users have only the necessary permissions to perform their tasks, minimizing security risks.
- Disable inactive accounts: Deactivate accounts that are no longer in use to prevent unauthorized access.
Conclusion
Understanding user activity on a Windows system is essential for maintaining system security, optimizing resource allocation, and ensuring efficient operations. By utilizing the methods and tools outlined above, administrators and users can gain valuable insights into user behavior, enabling informed decisions to enhance system security and optimize resource utilization. Proactive management of user accounts and system security measures contribute to a robust and secure digital environment.


Closure
Thus, we hope this article has provided valuable insights into Understanding User Activity on Windows: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!
