Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users
Related Articles: Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users
- 2 Introduction
- 3 Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users
- 3.1 Methods for Identifying Logged-in Users on Windows
- 3.2 Importance of Monitoring Logged-in Users
- 3.3 FAQs about Monitoring Logged-in Users
- 3.4 Tips for Monitoring Logged-in Users
- 4 Closure
Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users
In today’s interconnected world, maintaining the security and integrity of your computer systems is paramount. One essential aspect of this endeavor is understanding who is accessing your Windows devices and what activities they are undertaking. This knowledge empowers you to identify potential security threats, troubleshoot performance issues, and manage user access effectively.
This guide provides a comprehensive overview of the various methods available to monitor and identify logged-in users on Windows systems. We will delve into the different tools and techniques employed, exploring their functionalities and limitations. Furthermore, we will discuss the importance of user activity monitoring in various scenarios, highlighting its benefits and potential applications.
Methods for Identifying Logged-in Users on Windows
There are several methods available to view the list of currently logged-in users on a Windows computer. These methods range from simple built-in tools to advanced administrative utilities, each offering a different level of detail and functionality.
1. Task Manager:
The Task Manager, accessible by pressing Ctrl+Shift+Esc, provides a quick overview of currently running processes and applications. While not explicitly dedicated to user monitoring, the "Users" tab within the Task Manager displays a list of logged-in users along with their associated processes. This method is a convenient starting point for a basic understanding of user activity.
2. Logon Users:
The "Logon Users" utility, accessible through the Run dialog box (Win+R) by typing "lusrmgr.msc", provides a more detailed view of logged-in users. This tool displays information such as the user’s account name, domain, and session ID. It is a useful tool for administrators who need a more comprehensive view of user activity.
3. Command Prompt:
The command prompt offers a powerful and versatile method for monitoring user activity. By using the command "quser", you can obtain a list of logged-in users along with their session IDs, logon times, and idle times. This command provides a wealth of information for troubleshooting and analysis.
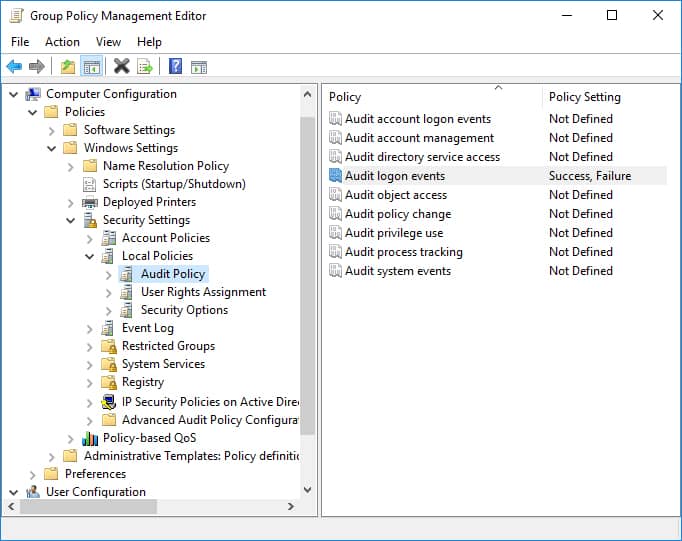
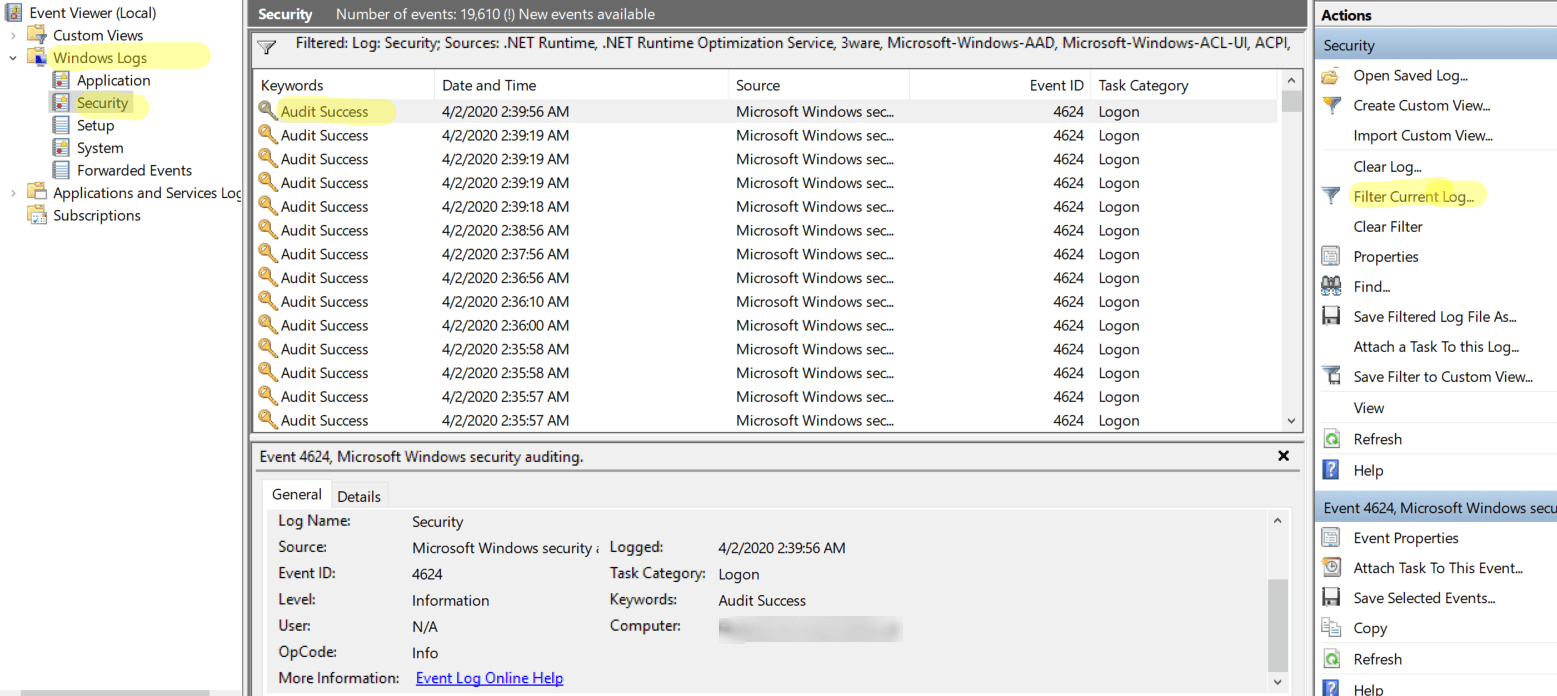
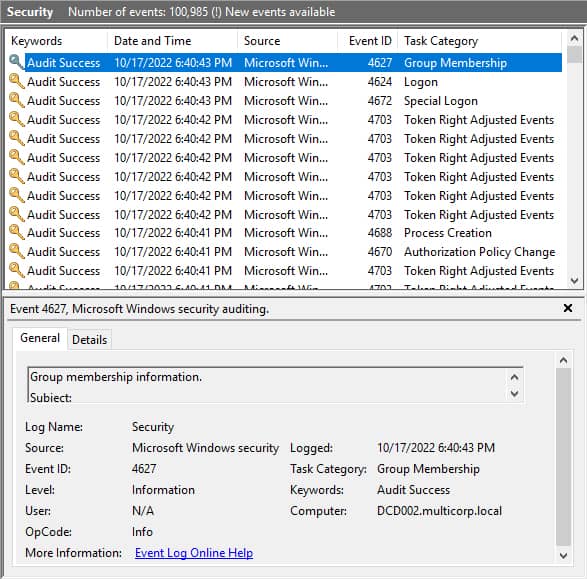
4. Event Viewer:
The Event Viewer, accessible through the Administrative Tools folder in the Control Panel, records various system events, including user logins and logouts. By examining the security logs within the Event Viewer, you can identify the specific times when users logged in and out of the system. This method offers a detailed historical record of user activity.
5. Remote Desktop Connection:
If you are managing a remote computer, you can use the Remote Desktop Connection to view the list of logged-in users. Once connected to the remote machine, you can access the Task Manager or the "Logon Users" utility as described above to monitor user activity.
6. PowerShell:
For advanced users, PowerShell offers a powerful scripting environment for managing and monitoring Windows systems. Using PowerShell cmdlets such as "Get-WmiObject Win32_ComputerSystem" and "Get-Process", you can retrieve information about logged-in users, their processes, and system resources.
7. Third-Party Monitoring Software:
Several third-party software solutions offer comprehensive user activity monitoring capabilities. These tools typically provide real-time tracking of user sessions, application usage, website visits, and other activities. They often offer advanced features such as reporting, alerts, and customizable filters, making them valuable for security and productivity management.
Importance of Monitoring Logged-in Users
Understanding user activity on Windows systems is crucial for various reasons, ranging from security and compliance to performance optimization and troubleshooting.
1. Security:
Monitoring logged-in users is essential for identifying potential security threats. By tracking user activity, you can detect unauthorized access attempts, suspicious logins, or unusual behavior that could indicate malware infection or malicious activity. This information allows you to respond promptly to threats and mitigate potential damage.
2. Compliance:
In many industries, regulatory requirements mandate the monitoring of user activity for compliance purposes. For example, financial institutions, healthcare providers, and government agencies are often required to track user access to sensitive data and systems to comply with industry regulations and data privacy laws.
3. Performance Optimization:
Monitoring logged-in users can help identify resource-intensive processes or applications that may be impacting system performance. By understanding which users are consuming the most resources, you can optimize system settings, prioritize workloads, or address performance bottlenecks.
4. Troubleshooting:
Monitoring user activity can aid in troubleshooting system issues. By identifying the users who were logged in at the time of a problem, you can gather valuable information about their actions, the applications they were using, and the resources they were accessing. This information can help pinpoint the root cause of the problem and facilitate faster resolution.
5. User Management:
Monitoring logged-in users can provide valuable insights into user behavior and resource consumption. This information can be used to optimize user accounts, enforce access policies, and manage user privileges effectively.
FAQs about Monitoring Logged-in Users
1. Is it legal to monitor user activity on a Windows computer?
The legality of monitoring user activity depends on the specific circumstances and applicable laws. Generally, employers are permitted to monitor employee activity on company-owned devices, but they must inform employees about the monitoring policy and comply with data privacy regulations. Similarly, parents may monitor their children’s activity on family computers, but they should be aware of potential privacy concerns.
2. What information can be gathered through user activity monitoring?
The information gathered through user activity monitoring can vary depending on the methods employed. Typically, it includes user login and logout times, the applications they use, the websites they visit, the files they access, and their keystrokes.
3. Are there any privacy concerns associated with user activity monitoring?
Yes, there are significant privacy concerns associated with user activity monitoring. It is crucial to ensure that monitoring is conducted ethically and legally, with appropriate transparency and consent. It is also important to protect the collected information from unauthorized access and use.
4. How can I prevent my activity from being monitored?
There are several ways to limit the amount of information that can be gathered about your activity on a Windows computer. These include using privacy-enhancing tools, disabling unnecessary tracking features, and being mindful of the information you share online.
5. What are the best practices for monitoring user activity?
Best practices for monitoring user activity include:
- Transparency: Clearly inform users about the monitoring policy.
- Legality: Ensure compliance with all applicable laws and regulations.
- Purposefulness: Only monitor activity that is relevant to the stated purpose.
- Minimization: Collect only the necessary information.
- Security: Protect the collected information from unauthorized access.
- Retention: Implement a policy for data retention and deletion.
Tips for Monitoring Logged-in Users
1. Use a combination of methods: Employ multiple methods for monitoring user activity to gain a comprehensive understanding.
2. Set up alerts: Configure alerts for unusual activity, such as suspicious logins, excessive resource consumption, or unauthorized access attempts.
3. Review logs regularly: Regularly review system logs to identify potential security threats and performance issues.
4. Use third-party tools strategically: Consider using third-party monitoring software for advanced features and reporting capabilities.
5. Stay informed: Stay up-to-date on best practices for user activity monitoring and security threats.
Conclusion
Monitoring logged-in users on Windows systems is an essential aspect of maintaining security, compliance, and system performance. By utilizing the various methods and tools discussed in this guide, you can effectively track user activity, identify potential threats, and optimize system resources. Remember to prioritize user privacy, comply with applicable laws and regulations, and implement robust security measures to protect the information gathered. Through a comprehensive approach to user activity monitoring, you can safeguard your Windows systems and ensure a secure and productive computing environment.



Closure
Thus, we hope this article has provided valuable insights into Understanding User Activity on Windows: A Comprehensive Guide to Monitoring Logged-in Users. We appreciate your attention to our article. See you in our next article!
