Understanding User Activity on Windows Server: A Comprehensive Guide
Related Articles: Understanding User Activity on Windows Server: A Comprehensive Guide
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Understanding User Activity on Windows Server: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding User Activity on Windows Server: A Comprehensive Guide

Windows Server, a robust and versatile operating system, provides a platform for managing and accessing critical resources. To ensure security and optimize performance, it’s essential to understand who is logged in and what activities they are performing. This information provides valuable insights into system usage, potential security risks, and resource allocation.
Understanding the Concept of User Sessions
On a Windows Server, a user session represents a connection established by a user to the server. This connection allows the user to access and interact with the server’s resources, including files, applications, and network services. Each user session is unique and is associated with a specific user account.
Identifying Logged-in Users
Several methods can be employed to identify users currently logged into a Windows Server:
- Server Manager: This built-in tool provides a comprehensive overview of the server’s status, including a list of logged-in users.
-
Command Prompt: Using the
query usercommand, administrators can retrieve detailed information about logged-in users, including their session ID, logon time, and terminal server name. - Remote Desktop Services: When utilizing Remote Desktop Services, administrators can view connected users and their sessions through the Remote Desktop Session Host (RDSH) Manager.
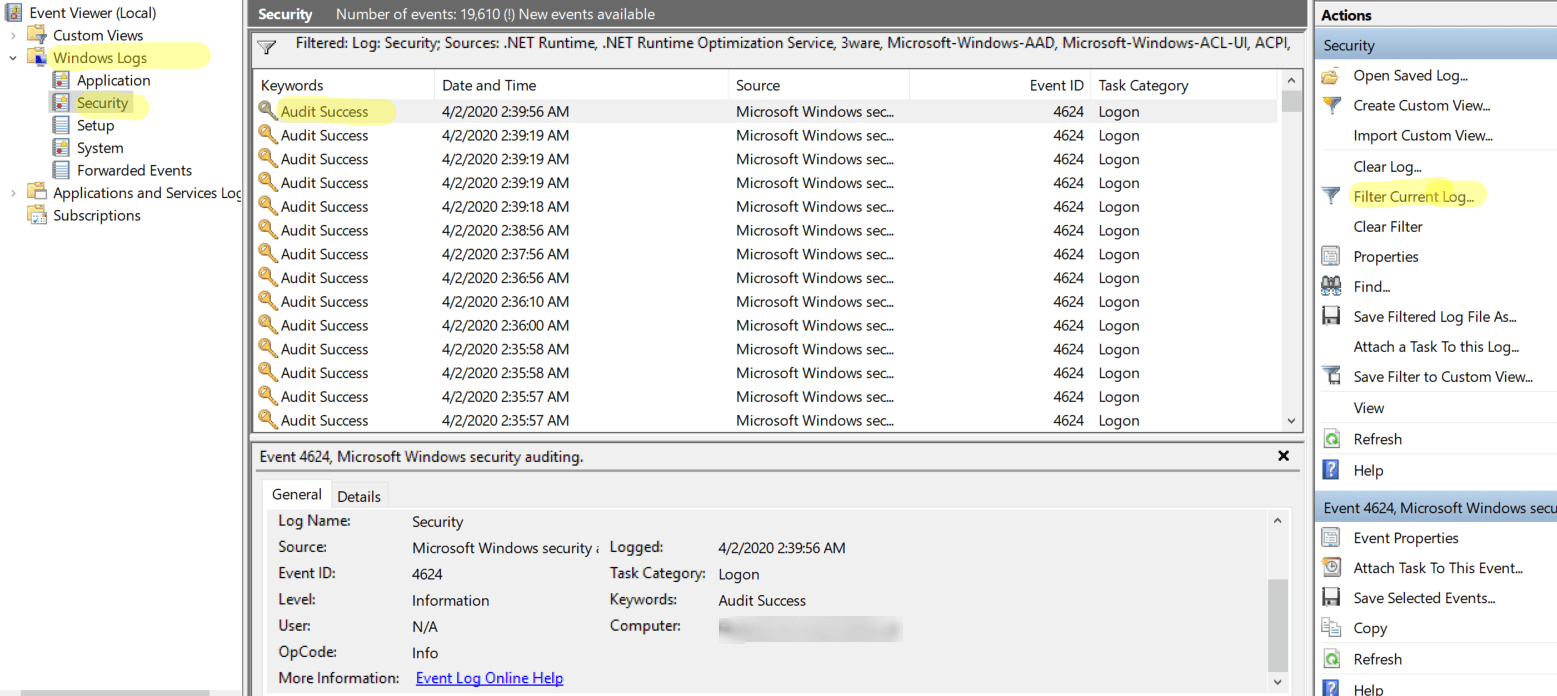
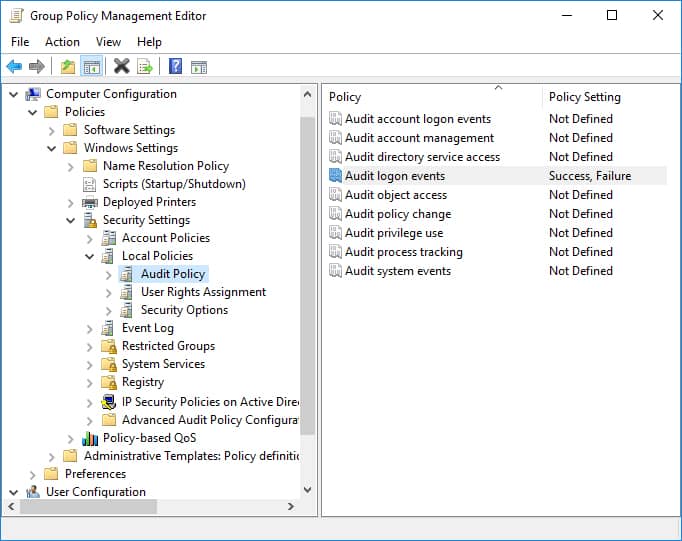
- Event Viewer: The Windows Event Viewer logs various system events, including user logon and logoff actions. This provides a detailed audit trail of user activity.
Benefits of Monitoring User Activity
Understanding user activity on a Windows Server offers numerous benefits, including:
- Enhanced Security: Tracking user sessions allows administrators to identify potential security breaches. Abnormal activity, such as multiple failed login attempts or access to sensitive files by unauthorized users, can trigger security alerts and prompt investigations.
- Resource Optimization: Monitoring user activity provides insights into resource utilization. Identifying users consuming excessive resources, such as CPU or memory, can help optimize system performance and prevent bottlenecks.
- Performance Troubleshooting: When performance issues arise, understanding user activity can help pinpoint the root cause. For example, if a specific user’s session is causing performance degradation, administrators can take appropriate steps to resolve the issue.
- Compliance and Auditing: In regulated industries, tracking user activity is crucial for compliance purposes. Detailed logs of user sessions provide evidence of user actions, enabling administrators to demonstrate adherence to security and compliance standards.
FAQs
Q: How can I prevent unauthorized users from accessing the server?
A: Implementing strong passwords, multi-factor authentication, and access control policies can effectively restrict unauthorized access to the server.
Q: How do I determine if a user has been inactive for a prolonged period?
A: By reviewing user session details, administrators can identify users who have been inactive for extended durations. This information can be used to automatically log users off or trigger alerts for further investigation.
Q: What are the best practices for managing user accounts on a Windows Server?
A: Best practices include:
- Principle of Least Privilege: Grant users only the permissions they require to perform their tasks.
- Regular Password Changes: Enforce frequent password changes to mitigate security risks.
- Account Lockout Policies: Configure account lockout policies to prevent brute-force attacks.
- Account Auditing: Regularly audit user accounts to ensure proper configuration and identify potential security vulnerabilities.
Tips for Effective User Activity Monitoring
- Establish Clear Policies: Define clear policies regarding user access, acceptable usage, and security procedures.
- Utilize Monitoring Tools: Implement monitoring tools designed to track user activity and provide alerts for suspicious behavior.
- Regularly Review Logs: Regularly review event logs to identify potential security threats and performance issues.
- Automate Tasks: Automate tasks such as user account management and security alerts to streamline operations.
- Train Users: Educate users on security best practices and responsible server usage.
Conclusion
Understanding user activity on a Windows Server is crucial for maintaining security, optimizing performance, and ensuring compliance. By implementing effective monitoring strategies, administrators can gain valuable insights into system usage, identify potential threats, and proactively manage the server environment. By combining strong security practices with proactive monitoring, organizations can effectively protect their critical data and ensure the reliable operation of their Windows Server infrastructure.


Closure
Thus, we hope this article has provided valuable insights into Understanding User Activity on Windows Server: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!
