Unlocking Network Access: Understanding and Managing Windows Firewall Port Permissions
Related Articles: Unlocking Network Access: Understanding and Managing Windows Firewall Port Permissions
Introduction
With great pleasure, we will explore the intriguing topic related to Unlocking Network Access: Understanding and Managing Windows Firewall Port Permissions. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking Network Access: Understanding and Managing Windows Firewall Port Permissions
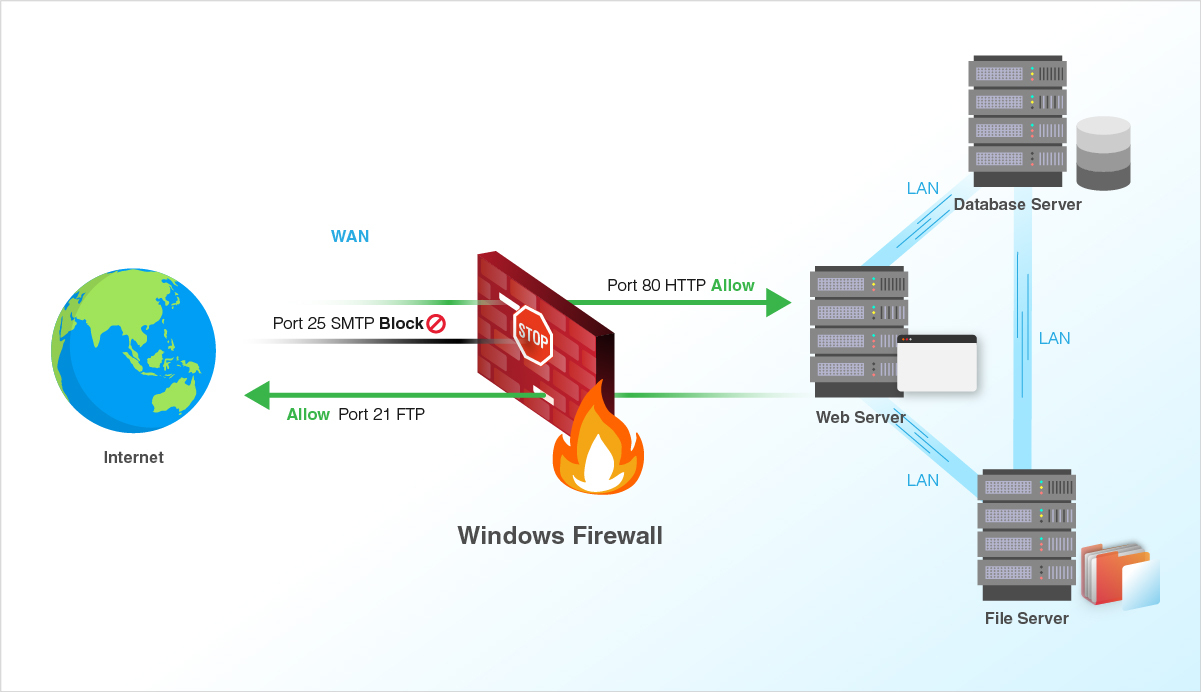
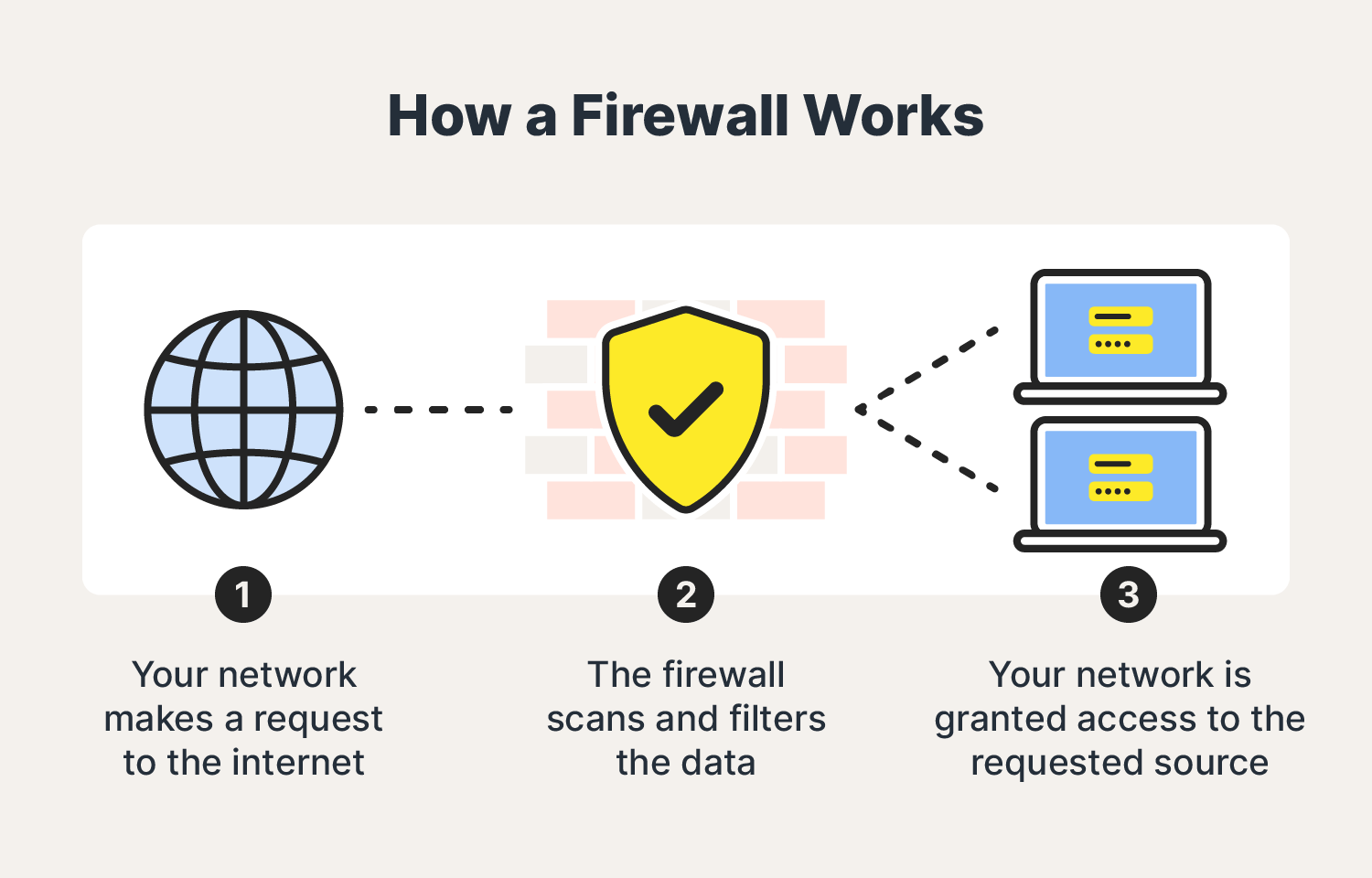
The Windows Firewall acts as a digital gatekeeper, diligently scrutinizing incoming and outgoing network traffic to protect your computer from malicious actors. While its primary function is to enhance security, it can sometimes impede the smooth operation of applications and services that require specific network access. This is where the concept of port permissions comes into play.
Port Permissions: The Foundation of Network Communication
Imagine your computer as a bustling city, with each application and service residing in a specific building. Ports, in this analogy, are the doorways to these buildings. When an application needs to communicate with another computer or service on the network, it sends data through a designated port.
The Windows Firewall, acting as the city’s vigilant guard, checks the identity of each incoming request. If the request is deemed safe, the firewall opens the relevant port, allowing the data to reach the intended application. However, if the request appears suspicious or unauthorized, the firewall blocks it, safeguarding your computer.
Why Allow Specific Ports?
While the default Windows Firewall settings are generally sufficient for basic protection, certain applications and services require specific ports to function correctly. For instance:
- Remote Desktop: This service allows you to control your computer remotely, using a program like Remote Desktop Connection. It typically uses port 3389.
- Web Servers: Websites hosted on your computer require specific ports, such as port 80 for HTTP and port 443 for HTTPS, to serve web pages to users on the internet.
- File Sharing Services: Sharing files over the network often relies on specific ports, such as port 139 and port 445 for SMB (Server Message Block).
- Gaming: Online games frequently use specific ports for communication and matchmaking.
The Importance of Port Permissions
Allowing specific ports can offer several benefits:
- Enhanced Functionality: Enables applications and services to function correctly, facilitating remote access, file sharing, and online gaming.
- Increased Network Access: Opens your computer to specific network services, facilitating communication with other devices and services.
- Improved User Experience: Enables smooth operation of applications and services that require specific network access, enhancing user productivity and satisfaction.
Understanding the Risks
While granting port permissions can enhance functionality, it’s crucial to understand the associated risks:
- Increased Vulnerability: Opening ports creates potential entry points for malicious actors, who can exploit vulnerabilities to gain unauthorized access to your computer.
- Data Breaches: Allowing unverified applications and services access to your computer can expose your sensitive data to unauthorized access.
- Security Compromises: Improper port configuration can leave your computer vulnerable to attacks, potentially leading to data loss, system instability, and financial losses.
Navigating the Windows Firewall: A Guide to Port Permissions
To manage port permissions in Windows, follow these steps:
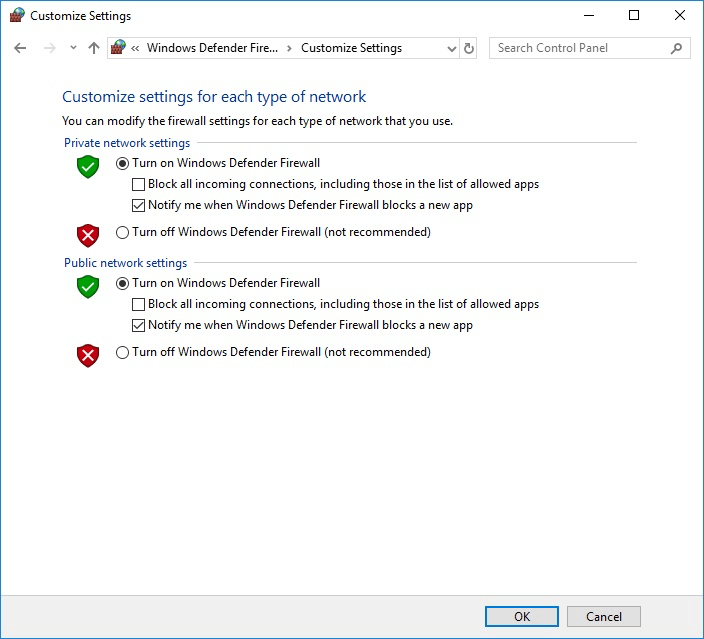
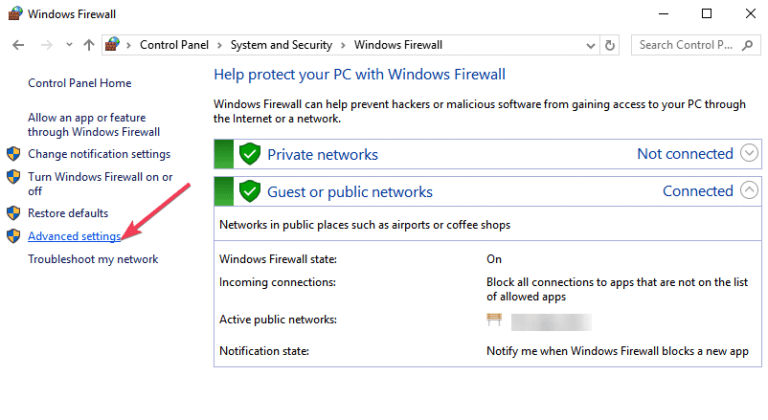
- Open Windows Firewall: Search for "Windows Firewall" in the Start Menu and select the top result.
- Choose Advanced Settings: Click on "Advanced settings" in the left pane.
- Navigate to Inbound Rules: In the left pane, expand "Inbound Rules" and select "New Rule."
- Select Rule Type: Choose "Port" as the rule type.
- Specify Protocol and Port: Select the appropriate protocol (TCP or UDP) and specify the port number.
- Define Action: Choose "Allow the connection" to grant access.
- Specify Profiles: Select the profiles for which the rule should apply (e.g., Domain, Private, Public).
- Provide a Name and Description: Give the rule a descriptive name and optional description.
- Create the Rule: Click "Finish" to create the new rule.
Tips for Secure Port Management
- Restrict Port Access: Only allow ports necessary for essential applications and services.
- Use Strong Passwords: Securely protect your computer and network with robust passwords.
- Keep Software Updated: Regularly update your operating system and applications to patch security vulnerabilities.
- Implement a Firewall: Use a reputable firewall to filter incoming and outgoing network traffic.
- Monitor Network Activity: Regularly monitor your network activity for suspicious behavior.
Frequently Asked Questions
Q: Can I allow multiple ports simultaneously?
A: Yes, you can create multiple rules to allow access to various ports for different applications and services.
Q: Can I block specific ports?
A: Yes, you can create rules to block specific ports, restricting access to specific applications and services.
Q: How can I determine which ports are used by specific applications?
A: You can use the "Resource Monitor" tool in Windows to view the ports used by running applications.
Q: Is it safe to allow all ports?
A: No, allowing all ports significantly increases your computer’s vulnerability to attacks. Only allow ports necessary for essential applications and services.
Q: What are the risks of allowing ports?
A: Allowing ports can increase vulnerability to attacks, expose your data to unauthorized access, and compromise your computer’s security.
Conclusion
Managing port permissions in Windows Firewall is crucial for balancing security and functionality. By carefully selecting the ports to allow, you can enhance the operation of essential applications and services while minimizing the risks associated with increased network access. Remember, a well-configured firewall, combined with good security practices, is the cornerstone of a secure and efficient digital environment.



/GettyImages-96189552-5970efe122fa3a001039d6c6.jpg)
Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Access: Understanding and Managing Windows Firewall Port Permissions. We hope you find this article informative and beneficial. See you in our next article!
