Unveiling the Identity: Understanding User Sessions in Windows
Related Articles: Unveiling the Identity: Understanding User Sessions in Windows
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Identity: Understanding User Sessions in Windows. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Identity: Understanding User Sessions in Windows

Windows operating systems, renowned for their user-friendly interfaces, employ a robust system for managing user sessions. Each user, upon successfully logging into a Windows machine, enters a dedicated session, effectively creating a personalized environment within the operating system. This session serves as a container for the user’s data, settings, and running applications, ensuring a distinct experience for each individual.
Delving into the Realm of User Sessions
The concept of user sessions in Windows is crucial for security, resource management, and user experience. Each session provides a secure and isolated space for a user’s activities, preventing conflicts and ensuring data privacy. This isolation is achieved through a combination of mechanisms:
- User Profiles: Every user has a unique profile associated with their account. This profile stores personal settings, preferences, and application data, ensuring a tailored experience for each user.
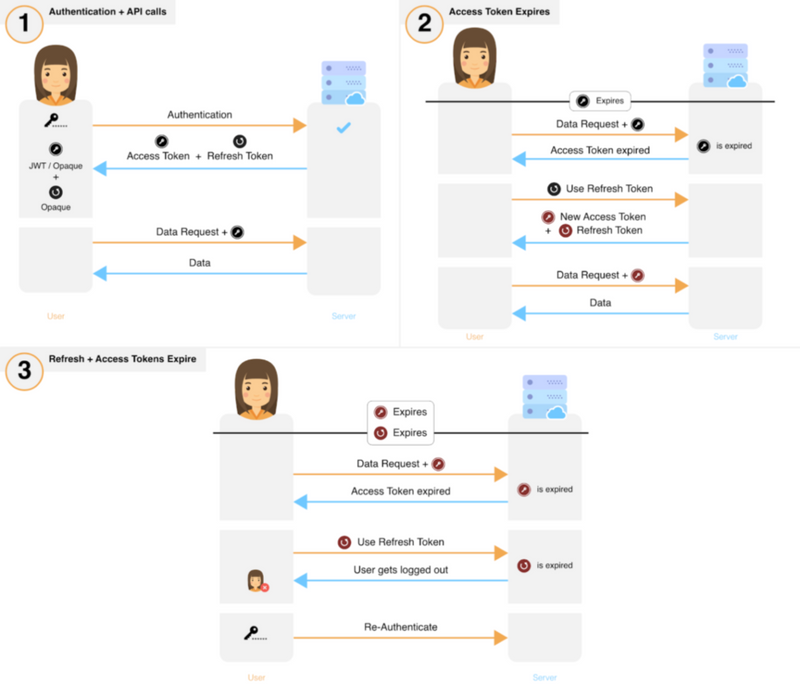
- Session Tokens: When a user logs in, Windows issues a unique session token, a digital identifier that verifies the user’s identity and privileges within the system. This token grants the user access to specific resources and applications based on their permissions.
- Virtualization: Windows employs virtualization techniques to isolate user sessions from each other. This ensures that processes running within one session cannot interfere with those in another.
Unveiling the Identity: Methods to Determine Logged-in Users
Several methods exist to identify the users currently logged into a Windows machine. These methods offer varying levels of detail and are suitable for different scenarios:
1. Task Manager: This readily available tool provides a concise overview of running processes and services. The "Users" tab within Task Manager displays the names of all logged-in users, along with their session IDs and login times.
2. Command Prompt: The command prompt, a powerful tool for interacting with the operating system, offers a more detailed view of user sessions. The command "query user" lists all logged-in users, including their session IDs, login times, and terminal services information.
3. Event Viewer: This tool records system events, including user logins and logouts. The "Security" log within Event Viewer provides detailed information about user authentication attempts, successful logins, and logoff events.
4. System Information: The "System Information" tool, accessible through the "System" control panel, provides a comprehensive overview of the system’s hardware and software configuration. This information includes a list of logged-in users and their associated session IDs.
5. Remote Desktop: Administrators can use remote desktop tools to connect to a Windows machine and view the logged-in users. This method allows for remote monitoring and troubleshooting of user sessions.
Understanding the Importance: The Benefits of User Session Management
The implementation of user sessions in Windows offers several key benefits:
1. Enhanced Security: User sessions provide a secure environment for user activities, isolating them from other users and preventing unauthorized access to sensitive data.
2. Resource Management: By separating user sessions, Windows can effectively manage system resources, ensuring that each user has access to the necessary resources for their tasks.
3. Improved User Experience: User sessions enable personalized settings and preferences, creating a tailored experience for each user. This customization enhances productivity and user satisfaction.
4. Application Isolation: User sessions prevent conflicts between applications running under different user accounts, ensuring stability and preventing data corruption.
5. Audit and Monitoring: The detailed information provided by user session logs allows for effective audit and monitoring of system usage, enabling administrators to identify potential security threats or resource bottlenecks.
FAQs Regarding User Sessions
Q1: What happens when a user logs out?
A: When a user logs out, their session is terminated. All running applications are closed, and the user’s data is saved. The user’s session token is revoked, and the user’s account is no longer active.
Q2: Can multiple users log in to the same computer?
A: Yes, multiple users can log in to the same computer, each creating their own separate session. This allows for shared access to the computer while maintaining user privacy and security.
Q3: How do I access a user’s session remotely?
A: Administrators can use remote desktop tools to connect to a Windows machine and access a specific user’s session. This allows for remote monitoring, troubleshooting, and assistance.
Q4: What are the different types of user accounts?
A: Windows offers different types of user accounts with varying levels of privileges. These include administrator accounts, standard user accounts, and guest accounts. Each account type has specific permissions and access rights.
Q5: What is a session ID?
A: A session ID is a unique identifier assigned to each user session. It serves as a reference point for tracking and managing user sessions within the system.
Tips for Managing User Sessions
1. Regularly Review User Accounts: Ensure that only authorized users have access to the system and that their account privileges are appropriate for their roles.
2. Implement Strong Passwords: Encourage users to create strong passwords and regularly change them to enhance security.
3. Use User Account Control (UAC): Enable UAC to prompt users for confirmation before making system-level changes, reducing the risk of unauthorized modifications.
4. Monitor User Session Logs: Regularly review user session logs to identify potential security threats, resource bottlenecks, or unusual activity.
5. Implement Remote Access Policies: Define clear policies for remote access to user sessions, ensuring security and compliance with company regulations.
Conclusion
User sessions are an integral part of the Windows operating system, providing a secure, efficient, and personalized environment for each user. By understanding the principles behind user sessions and implementing best practices for their management, administrators can ensure a secure and productive environment for all users. The robust mechanisms employed by Windows for session management contribute to the overall stability, security, and user experience of the operating system.


Closure
Thus, we hope this article has provided valuable insights into Unveiling the Identity: Understanding User Sessions in Windows. We appreciate your attention to our article. See you in our next article!
